To ensure the confidentiality, integrity, availability, and legitimacy of information assets (hardware, software, data, documents, and personnel related to information processing), prevent willful or accidental internal or external threats, MetaAge has effectively reduced the risks of information and communication assets being stolen, used improperly, disclosed, altered, or damaged due to manned negligence or intentional or natural disasters.

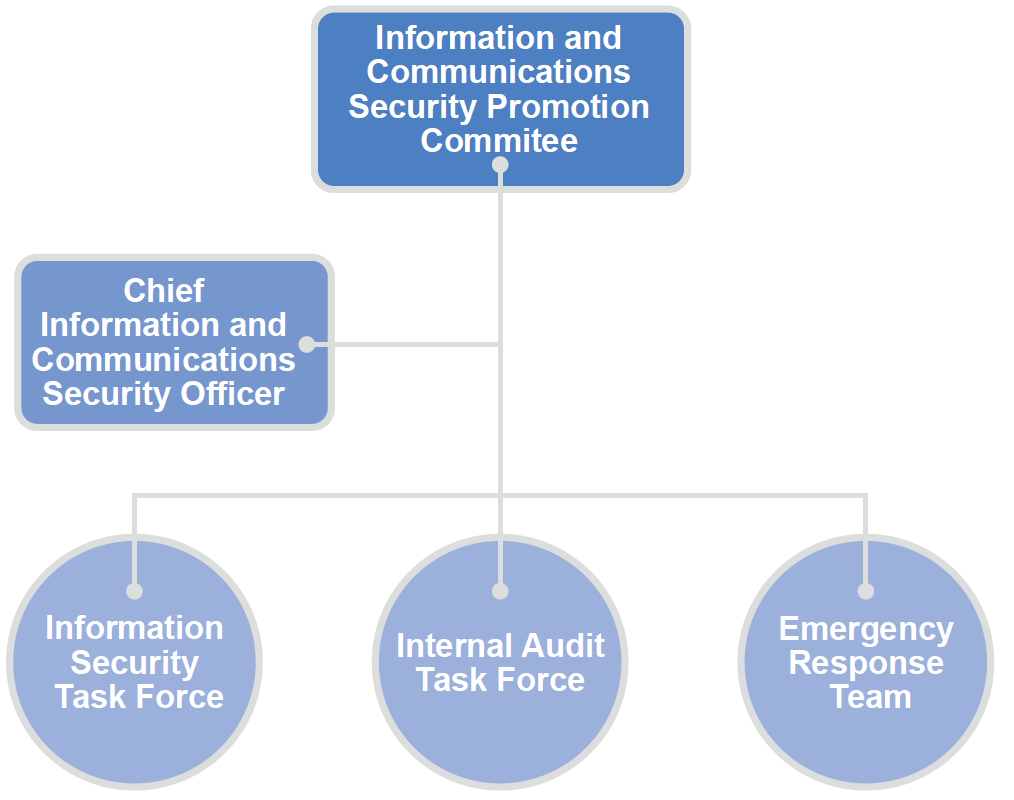
MetaAge has established an Information and Communications Security Promotion Committee, composed of the Chief Information and Communications Security Officer as convener and department heads as members. The committee holds regular meetings to coordinate the development, implementation, risk management, and review of information security policies. A review meeting on information and communications security management was held on March 4, 2024.
We deeply understand the importance of privacy and are thus committed to ensuring, respecting, and protecting customer privacy and trade secrets. Except for definite authorization or legal requests, we will not disclose or use the privacy or trade secrets off customers for any purpose. We have established the “Information and Communication Security Inspection Management Regulations”, built a secure and trusted IT environment, and equipped the IT environment with various information and communication security equipment such as firewalls and antivirus systems to ensure the security of corporate IT data, systems, equipment, and networks and thereby protect customer privacy data.
To ensure a secure and trustworthy IT environment, MetaAge has established the “Information and Communications Security Inspection Management Measures” and implemented safeguards such as firewalls and antivirus systems to protect data, systems, equipment, and networks—safeguarding customer privacy.
MetaAge has established a “Code of Ethical Conduct for Employees,” which requires employees to carefully manage all confidential information obtained during their duties. Such information must not be disclosed or used for non-work purposes, even after resignation, unless authorized by the Company or necessary for job execution. To prevent unauthorized disclosure due to personal actions, employees are also required to sign a personal data consent form to protect customer rights and prevent misuse of information by third parties.
The Company protects customer data with strict controls and regularly promotes information security awareness through internal emails and onboarding training. Confidential documents are access-controlled; non-designated personnel must obtain supervisor approval. Annual checks are conducted to prevent loss of complaint-related data, with reviews and improvements made if issues arise.